halesec
Cloud. Security. Dogs.
Not necessarily in that order.
PGP: 0xC0EE29073A219F19
My Shmoocon Retrospective
by James Hale
Back to reality after Shmoocon 2018, which was easily the best con that I’ve been to so far. I got more out of Day 1 of Shmoocon than I did out of entire week of some certain other large cloud-y conferences. Granted, this was my very first con in the InfoSec space, so that may have had something to do with it, but overall, I loved the format, the talks, the people, and the extracurricular activities (CTF, Lockpick Village, etc). I loved it so much that I wanted to do an incredibly disjointed write-up on my experience. Enjoy!
Shmoocon was my first con experience as a local. I live right up the street from the venue, in Adams Morgan, so I would have had a tough time justifying the cost of the hotel (and my absence) to my wife. That said, I do feel like I missed out on some of the late-night shenanigans because I was trekking back to my apartment each night. That wasn’t really a detractor from an overall awesome con experience, just an observation.
This was apparently the first year that Shmoocon gave out electronic badges, which had a WiFi chip (ESP8266) on board that was initially flashed to be a site survey tool for the Con’s primary network. I wish that I had a stopwatch going, because the time it took for people to start disassembling their badges to try and hack them was a matter of minutes. It was amazing.

Opening Remarks
Like most of the other attendees, I piled into the center room, dubbed One Track Mind / Bring it On! for the opening remarks from Heidi and Bruce Potter. They started out with general con info, telling the n00bs (raises hand) how things work, the dos/do nots and more generally to not be an asshole. Heidi then turned the mic over to Bruce for his remarks which, from what I gather, tend to turn into a bit of a rant.
Bruce had a great overall message, and the point that stuck with me was how we, as infosec practitioners tend to blame “stupid users” when they make mistakes. In reality, it’s stupid infosec people who have this unrealistic expectation of users to not make these mistakes in the first place, rather than helping to set their world up so that they can try things out, screw them up, and learn from them, without the ability to cause real damage.
My favorite was the imagery of handing users a spiky ball with needles and poison and things sticking out of it, telling them that they can only touch one specific part of it, then being surprised when they slam their whole hand on it. This mindset of “guardrails” over “gates”, meaning don’t let them do dangerous shit, but also don’t make them come to you for everything, is something that I’ve seen become more prevalent lately and it’s also something that I’ve been trying to evangelize at work.
Lockpick Village
While the first talks started up, I meandered on over to the Lockpick Village (after buying a t-shirt and donating to my EFF peeps!) to try my hand at picking something other than the one crappy padlock at my house that I’ve done a zillion times over. The village was being run by TOOOL [toool.us] and that had knowledgeable staffers running around to the tables and teaching people the basics. This was a lot of fun and I managed to find time in each of my mornings to spend here.
CTF, CTF and more CTF
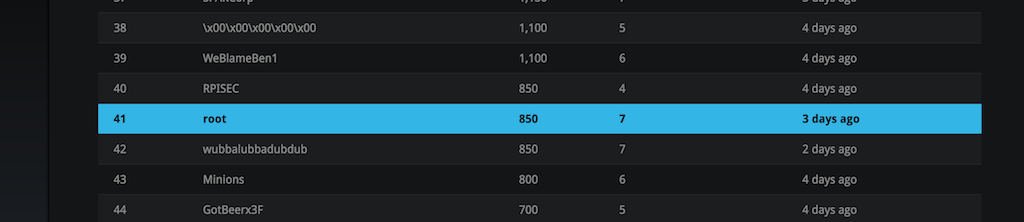
The Kaizen CTF is where I easily spent the majority of my time. My newly found CTF buddy, Emily, whom I met at one of my aforementioned Lockpick Village sessions, joined forces and set out to hack all the things. As it would turn out, we didn’t hack all the things, but we did hack many of the things. I got some of the coding flags, Emily smashed the crypto ones, and we each got one of the physical flags (lock picking, go figure!), plus a few others here and there. While I’ve done CTFs before (Vulnhub, Hackthebox, etc), it was never as part of an event or in a team. This was a great time and we both learned a lot from the challenges and each other. Finishing 41st out of 139 teams (93 teams if you only count those who started challenge after registering), ain’t too shabby either.
Talks
Shmoo is the first con that I’ve gone to where I didn’t feel like I needed to attend as many of the sessions as possible in order to get the most out of me being there. During my time there, I had a healthy mix of attending sessions, extracurriculars (CTFs, Lockpick Village, etc), networking and chatting with vendors. In my mind, attending sessions was a lower priority, since I knew that they would all be available online after the con is over. I’m not typically of the question-asking-in-a-large-crowd sort, so sessions don’t need to happen in real time for me. YMMV here.
That said, I genuinely enjoyed the Friday night Firetalks. The rapid-fire format and panel of judges was an interesting way to do things. I also learned that there’s a bit of a holy war surrounding the “correct” way to pronounce “CISO”. The night was capped off by @SecBarbie’s Firetalk on Scotch and Bubbles, which I thought was a great way to end the “official” evening.
Saturday, I bounced between talks and more rounds of CTF with my teammate. Some that I would recommend once the videos get posted:
- Nation-State Espionage: Hunting Multi-Platform APTs on a Global Scale (Belay It!)
- AWS Honey Tokens with SPACECRAB (Belay It!)
- OK Google, Tell Me About Myself (Build It!)
There are many more that I missed and are looking forward to watching once they come out.
- SIGINT on a budget: Listening in, gathering data and watching–for less than $100 (Build It!)
- Skill Building By Revisiting Past CVEs (Bring it On!)
- Hacking the News: an Infosec Guide to the Media, and How to Talk to Them (Bring it On!). <– Sean gave me a preview answer to this on Saturday morning: You don’t.
PARTY!
The party on Saturday night was a kick-ass good time. @SecBarbie and @KeithMyers kept the tunes going well past the point that I felt I needed to bow out and head home. I probably would have stayed later, had I been staying on-site at the hotel, but alas.
There’s photo with me in it floating around out there, but it wasn’t on my phone when we all parted ways. If someone reading this has a copy, send it to me please!
Polarity Challenge
The Polarity Challenge was a neat thing that was put on by PolarityIO. In your swag bag, everyone got a card with a 32-character hex string. Seven attendees had the same string and if you matched with someone, you each got a mini hackable drone. I tweeted my hash out and someone replied with a match, so we each got the first level prize. There were accessories to the drone that you could get with more matches, but by the time we found others with our hash, they were all out of the higher-level prizes.
Cons to my con experience
There were times that my social anxiety got the best of me. I walked into the Con on Friday, not knowing a soul there. That changed as the weekend went on, and I’m incredibly thankful for it, but the social events of Friday evening were really rough on that front and I eventually just bailed.
Summary
This was a great first InfoSec con experience for me, overall. Assuming that I’m able to lock down a ticket next year, I’m definitely going back! My key takeaway here is: while going to the talks has its obvious benefits, doing the non-session activities is how you meet people, make friends, and network.
Lastly, I want to give a huge shout out to Zack (@zfasel) of Urbane Security (@UrbaneSec) for hooking me up with a ticket sale and making my Shmoocon experience possible!
Some other cons on my list this year:
- BSidesNOVA
- BSidesCharm
- DEF CON (travel budget permitting)
- DerbyCon (my luck with ticket acquisition permitting)
- BSidesDC (missed 2017 because I was attending a wedding)
Next up: BSidesNOVA! See you there!
tags: conference - shmoocon